p.403
p.408
p.412
p.416
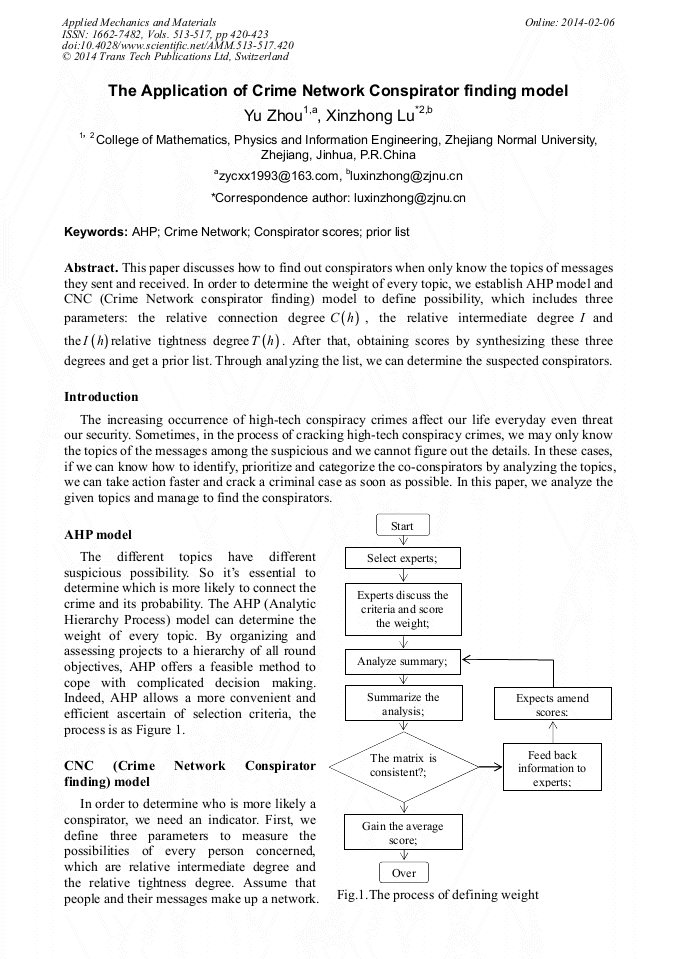
p.420
p.424
p.431
p.435
p.439
The Application of Crime Network Conspirator Finding Model
Abstract:
This paper discusses how to find out conspirators when only know the topics of messages they sent and received. In order to determine the weight of every topic, we establish AHP model and CNC (Crime Network conspirator finding) model to define possibility, which includes three parameters: the relative connection degreeC(h) , the relative intermediate degree I and the I(h)relative tightness degreeT(h). After that, obtaining scores by synthesizing these three degrees and get a prior list. Through analyzing the list, we can determine the suspected conspirators.
Info:
Periodical:
Pages:
420-423
Citation:
Online since:
February 2014
Authors:
Keywords:
Price:
Сopyright:
© 2014 Trans Tech Publications Ltd. All Rights Reserved
Share:
Citation: