p.920
p.923
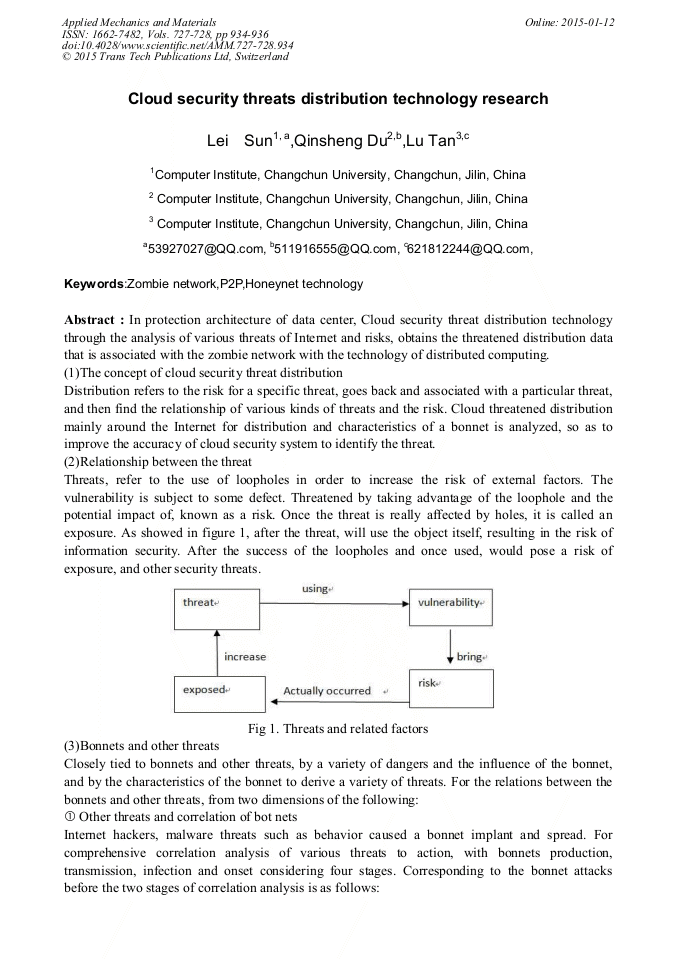
p.926
p.930
p.934
p.937
p.940
p.944
p.948
Cloud Security Threats Distribution Technology Research
Abstract:
Inprotection architecture of data center, Cloud security threat distributiontechnology through the analysis of various threats of Internet and risks,obtains the threatened distribution data that is associated with the zombienetwork with the technology of distributed computing.
Info:
Periodical:
Pages:
934-936
Citation:
Online since:
January 2015
Authors:
Keywords:
Price:
Сopyright:
© 2015 Trans Tech Publications Ltd. All Rights Reserved
Share:
Citation: