p.1061
p.1065
p.1069
p.1074
p.1081
p.1087
p.1091
p.1097
p.1101
Research on Architecture Survivability of Wireless Networks
Abstract:
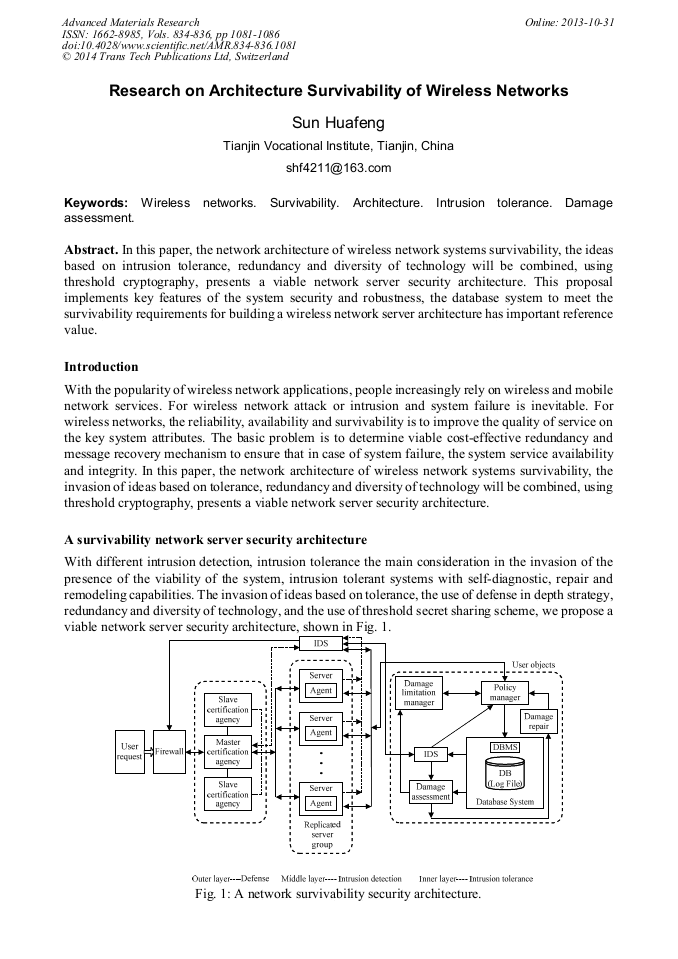
In this paper, the network architecture of wireless network systems survivability, the ideas based on intrusion tolerance, redundancy and diversity of technology will be combined, using threshold cryptography, presents a viable network server security architecture. This proposal implements key features of the system security and robustness, the database system to meet the survivability requirements for building a wireless network server architecture has important reference value.
Info:
Periodical:
Pages:
1081-1086
Citation:
Online since:
October 2013
Authors:
Price:
Сopyright:
© 2014 Trans Tech Publications Ltd. All Rights Reserved
Share:
Citation: