p.656
p.662
p.666
p.670
p.674
p.678
p.682
p.686
p.690
Research on the Zero-Bit Watermarking Algorithms Based on the Matrix Decomposition for Digital Images
Abstract:
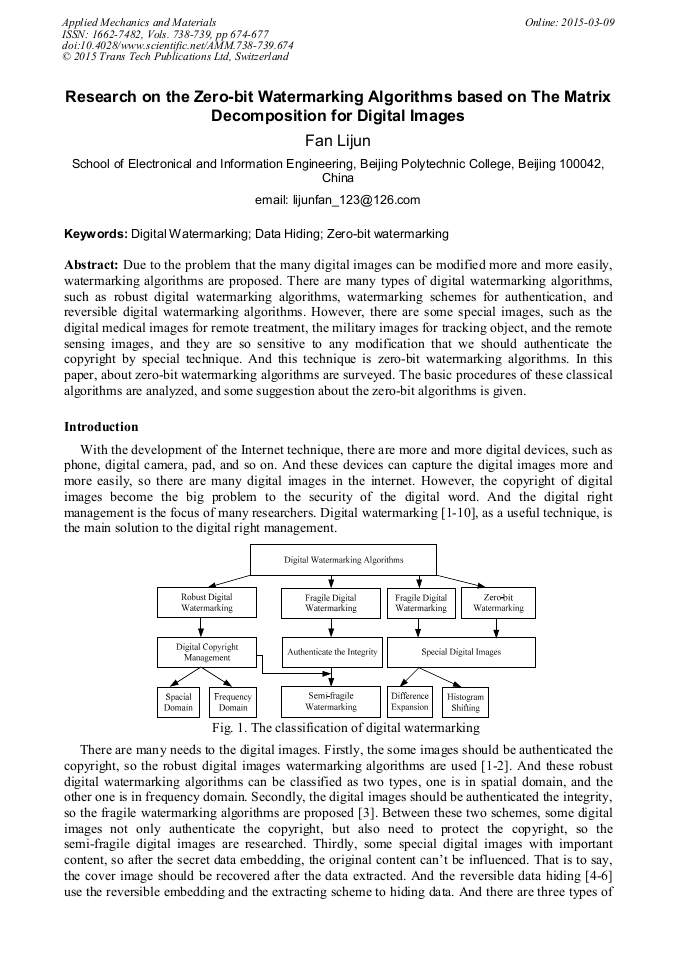
Due to the problem that the many digital images can be modified more and more easily, watermarking algorithms are proposed. There are many types of digital watermarking algorithms, such as robust digital watermarking algorithms, watermarking schemes for authentication, and reversible digital watermarking algorithms. However, there are some special images, such as the digital medical images for remote treatment, the military images for tracking object, and the remote sensing images, and they are so sensitive to any modification that we should authenticate the copyright by special technique. And this technique is zero-bit watermarking algorithms. In this paper, about zero-bit watermarking algorithms are surveyed. The basic procedures of these classical algorithms are analyzed, and some suggestion about the zero-bit algorithms is given.
Info:
Periodical:
Pages:
674-677
Citation:
Online since:
March 2015
Authors:
Keywords:
Price:
Сopyright:
© 2015 Trans Tech Publications Ltd. All Rights Reserved
Share:
Citation: