p.690
p.696
p.701
p.705
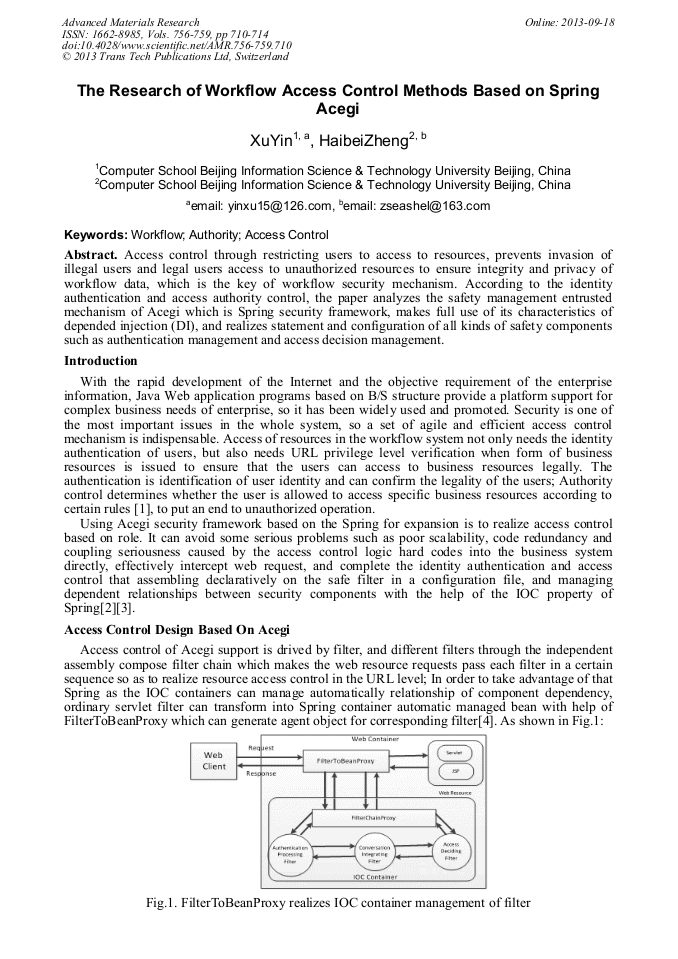
p.710
p.715
p.720
p.724
p.728
The Research of Workflow Access Control Methods Based on Spring Acegi
Abstract:
Access control through restricting users to access to resources, prevents invasion of illegal users and legal users access to unauthorized resources to ensure integrity and privacy of workflow data, which is the key of workflow security mechanism. According to the identity authentication and access authority control, the paper analyzes the safety management entrusted mechanism of Acegi which is Spring security framework, makes full use of its characteristics of depended injection (DI), and realizes statement and configuration of all kinds of safety components such as authentication management and access decision management.
Info:
Periodical:
Pages:
710-714
Citation:
Online since:
September 2013
Authors:
Keywords:
Price:
Сopyright:
© 2013 Trans Tech Publications Ltd. All Rights Reserved
Share:
Citation: