p.1620
p.1624
p.1628
p.1632
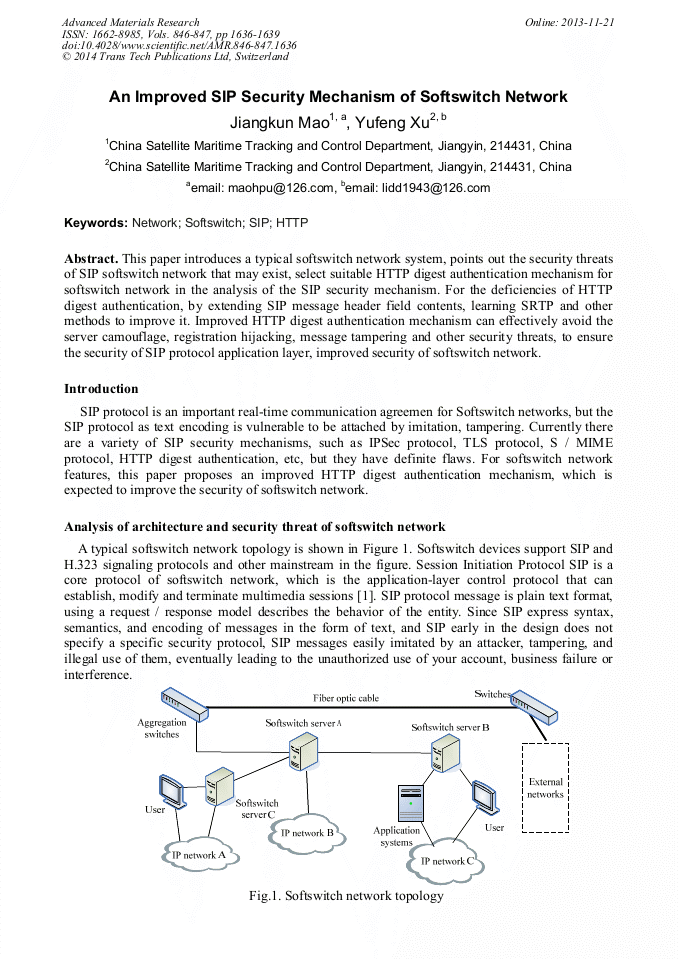
p.1636
p.1640
p.1644
p.1648
p.1652
An Improved SIP Security Mechanism of Softswitch Network
Abstract:
This paper introduces a typical softswitch network system, points out the security threats of SIP softswitch network that may exist, select suitable HTTP digest authentication mechanism for softswitch network in the analysis of the SIP security mechanism. For the deficiencies of HTTP digest authentication, by extending SIP message header field contents, learning SRTP and other methods to improve it. Improved HTTP digest authentication mechanism can effectively avoid the server camouflage, registration hijacking, message tampering and other security threats, to ensure the security of SIP protocol application layer, improved security of softswitch network.
Info:
Periodical:
Pages:
1636-1639
Citation:
Online since:
November 2013
Authors:
Keywords:
Price:
Сopyright:
© 2014 Trans Tech Publications Ltd. All Rights Reserved
Share:
Citation: