p.809
p.815
p.819
p.824
p.830
p.834
p.839
p.843
p.847
The Research and Implementation about AFIS
Abstract:
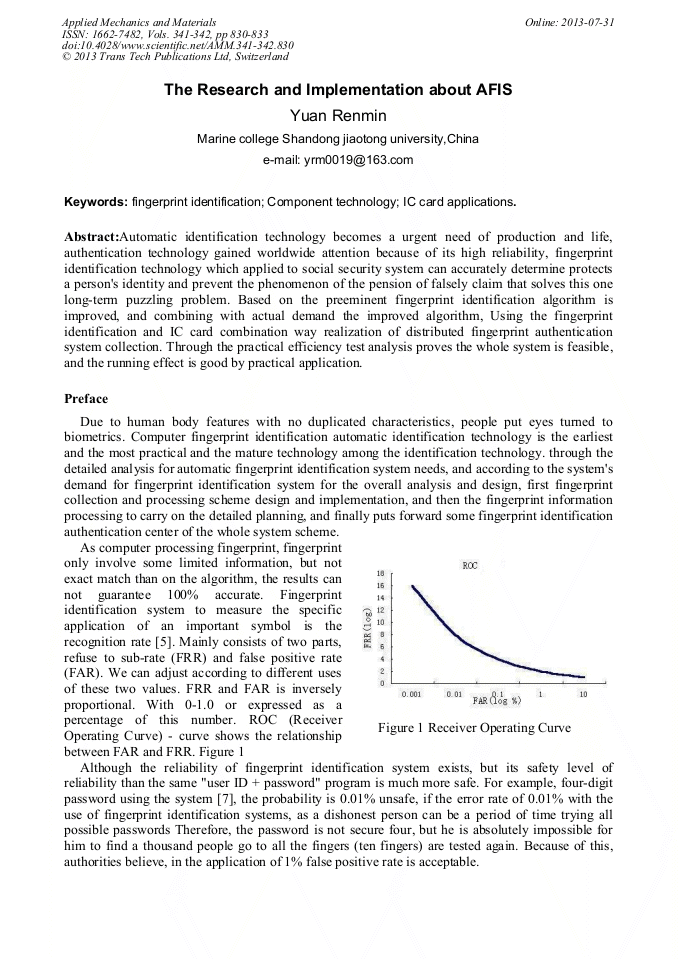
Automatic identification technology becomes a urgent need of production and life, authentication technology gained worldwide attention because of its high reliability, fingerprint identification technology which applied to social security system can accurately determine protects a person's identity and prevent the phenomenon of the pension of falsely claim that solves this one long-term puzzling problem. Based on the preeminent fingerprint identification algorithm is improved, and combining with actual demand the improved algorithm, Using the fingerprint identification and IC card combination way realization of distributed fingerprint authentication system collection. Through the practical efficiency test analysis proves the whole system is feasible, and the running effect is good by practical application.
Info:
Periodical:
Pages:
830-833
Citation:
Online since:
July 2013
Authors:
Price:
Сopyright:
© 2013 Trans Tech Publications Ltd. All Rights Reserved
Share:
Citation: