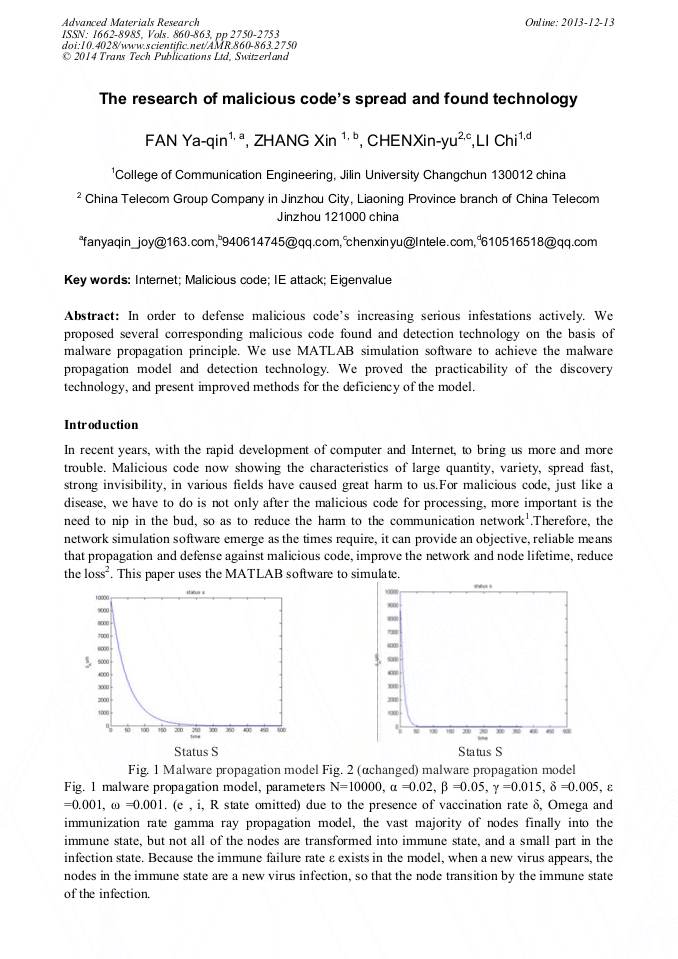
[1]
Jungsuk SONG etc. Cooperation of Intelligent Honeypots to Detect Unknown Malicious Codes[R]. WOMBAT Workshop on Information Security Threats Data Collection and Sharing. 2008: 31-33.
DOI: 10.1109/wistdcs.2008.10
Google Scholar
[2]
Bhavani Thuraisingham. Data Mining for Malicious Code Detection and Security Applications[R]. WI'09/IAT'09 Joint Invited TalksWI-IAT 2009. 2009: 6-11.
Google Scholar
[3]
Chen Zemao, Zhao Junge, Wu Xiaoping, Tang Weimin. Analyze and Model the Primitive Attacking Mechanisms of Malicious Codes[J]. International Symposium on Intelligent Information Technology Application Workshops, 2008(5), 527-532.
DOI: 10.1109/iita.workshops.2008.51
Google Scholar
[4]
Yang yue jiang Wang chang li, The spread of malicious software research and prevention[R]. 2010 Second International Workshop on Education Technology and Computer Science. 2010: 777-779.
DOI: 10.1109/etcs.2010.96
Google Scholar
[5]
ZHOU Zheng, ZHANG Yun. An Owner's Will Based Model against Malicious Attack[R]. 2009WASE International Conference on Information Engineering. 2009, 318-320.
Google Scholar
[6]
Melissa Chau, Kiranjeet Kaur, Wong Teck Zhung. Asia/Pacific(Excluding Japan)Mobile Phone 2011-2015 Forecast and Analysis[R]. IDC: IDC, 2011: 5-9.
Google Scholar
[7]
Qin Jia. The research of intelligent mobile terminal [D]. Wuhan: Wuhan University of Technology Computer Institute. 2010: 27-34.
Google Scholar
[8]
Tan Qing. A method of active defense executable malicious code and its realization [D]. Beijing: Beijing Jiaotong University,. 2007: 7-17.
Google Scholar
[9]
Chen Zemao, Shen Changxiang. Mechanism of malicious code and model [J]. computer engineering and design, (2008).
Google Scholar
[10]
Wang Xiaojie, Wang Haifeng. Application of malicious code detection algorithm based on semantic [J]. based on computer systems, 2009 (8): 103-105.
Google Scholar