p.561
p.565
p.570
p.575
p.580
p.584
p.588
p.592
p.596
Study on Computer Virus Search System Based on Content Addressable Memory
Abstract:
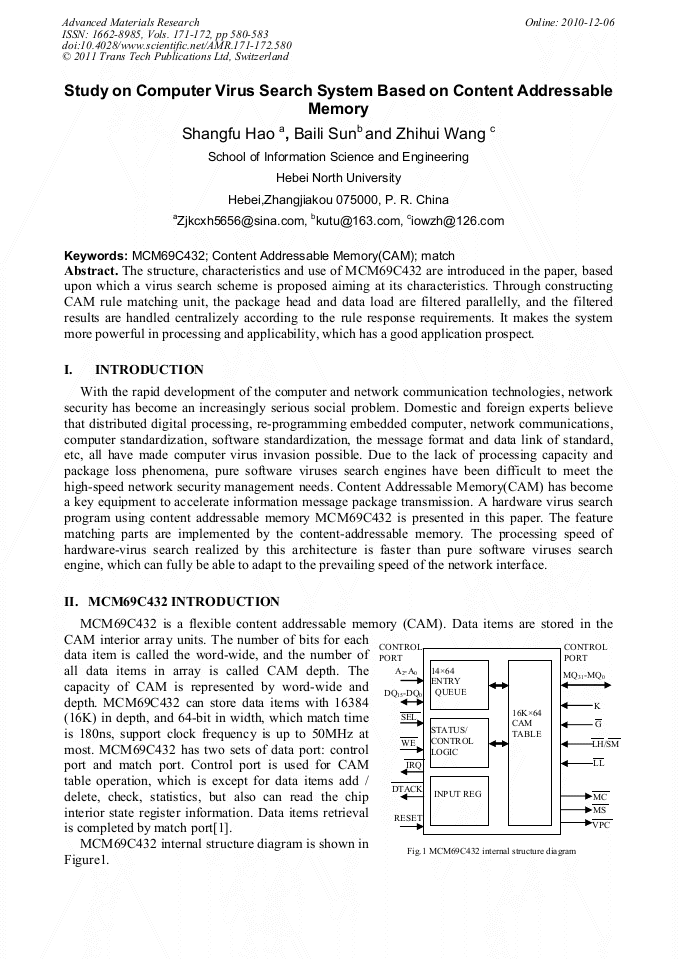
The structure, characteristics and use of MCM69C432 are introduced in the paper, based upon which a virus search scheme is proposed aiming at its characteristics. Through constructing CAM rule matching unit, the package head and data load are filtered parallelly, and the filtered results are handled centralizely according to the rule response requirements. It makes the system more powerful in processing and applicability, which has a good application prospect.
Info:
Periodical:
Pages:
580-583
Citation:
Online since:
December 2010
Authors:
Keywords:
Price:
Сopyright:
© 2011 Trans Tech Publications Ltd. All Rights Reserved
Share:
Citation: